This article is the second in a 3-part series: See it > Solve it > Share it
Cloud security may not be a new concept to many in the MSP industry, but the demand and challenges continue to grow. So, the future of MSP profitability relies on running an efficient and comprehensive security practice.
In October, SkyKick held an event to speak with partners from around the world on this opportunity and next evolution of cyber security. We discussed how best practices for MSPs lies in Intelligent Customer Protection, which can be framed in these 3 categories: “See it, Solve it, Share it.”
In this blog, we’ll focus on the second pillar of Intelligent Customer Protection that was discussed at the event, “Solve it”.
When “Solving It”, the Clock is Ticking
In cyber-security, “Solving it” needs to be consistent and easy. To scale a security management practice, MSPs should find tools that allow them to be efficient in the delivery of solutions without needing to hire additional personnel. Automation should also be cornerstone to their focus, allowing them to achieve that scalability. Additionally, you need tools that allow you to “Solve it” quickly.
Whether you’re helping a customer with a real cyber security incident, a simple ticket request by an end user, or you’re just performing pro-active security precautions, the speed at which you can “Solve it” is crucial.
We all know that during a cyber-attack, every second counts. While the customer is exposed to a threat or attack, emotions can run high. Customers value MSPs who can resolve a security incident quickly and thoroughly, so MSPs should be equipped with automation tools so they can run a comprehensive solution quickly.
The same can be said when an end-user has opened a less urgent security-related ticket with their MSP. Although less urgent than a security breach, their opinion of their experience is based on the swift fulfillment of their request, and the options or recommendations you present to them which they may not have known.
But even when performing proactive maintenance on a customer who may not have opened a ticket, the internal cost for MSPs can often be difficult to absorb without the right automation tools.
Speed impacts your customer’s perception of your services…as well as your internal costs.
Regardless of the trigger for a solution needing to be performed, the vetting and execution of the solution can be time-consuming. It requires expertise in knowing what to solve, where to solve it, and how to execute the solution. Security Manager was built to make it fast, easy, and repeatable for MSP teams to “Solve it”.
Workflows: How Security Manager Helps MSPs “Solve It”
In our first blog, we covered how Security Manager helps you “See It”, improving your visibility so you can quickly locate a cyber-security vulnerability which needs to be addressed. This visibility is available through robust dashboards and reports which allow you to view one or all of your customers – all in one place. Read More
Workflows are the next step in “See it, Solve it, Share it.” They were designed for MSPs to efficiently vet and perform powerful solutions against one or all of their customers.
Security Manager includes dozens of powerful out-of-the-box workflows available to you to deliver a comprehensive range of security solutions for today’s security climate. These workflows require no coding experience and contain detailed documentation for your team.
Each workflow is fully configurable, and for ease of use, they default to Microsoft recommendations and industry best practices.
Every Security Manager workflow contains the following features:
- An interactive list of powerful commands, displayed in sequence
- Layman explanations and links to Microsoft articles related to each of the commands
- Ability to run the workflow now or schedule in the future, with the option to make recurring
- Fully customizable with the ability to add commands and other steps to the workflow
- View status of workflows past, present, and future
- Drill-down details to see the actual code the command will run. This code is read/write (but configurable to read-only)
- Drag-and-drop code: Ability to re-order the commands with no coding required
Additionally, many workflows offer optional steps, such as reports and other workflow-specific optional commands, which you can toggle on/off based on the situation.
These Security Manager workflows are the “Solve it” automation which help MSPs provide their security practice’s comprehensive security management services with great efficiency, accuracy, and consistency.
At Your Fingertips
Workflows are made accessible in multiple locations within Security Manager. For example, Workflows are available in the “Analyze” dashboard of Security Manager by navigating to Security Manager => Manage => Workflows. Here Workflows are displayed in a “Solutions Panel” to the right of this dashboard to allow you to pivot from monitoring to taking action.
The Solutions Panel will display a dynamic context-based list of workflows to take action against the recommended actions in the dashboard. See it, then solve it:
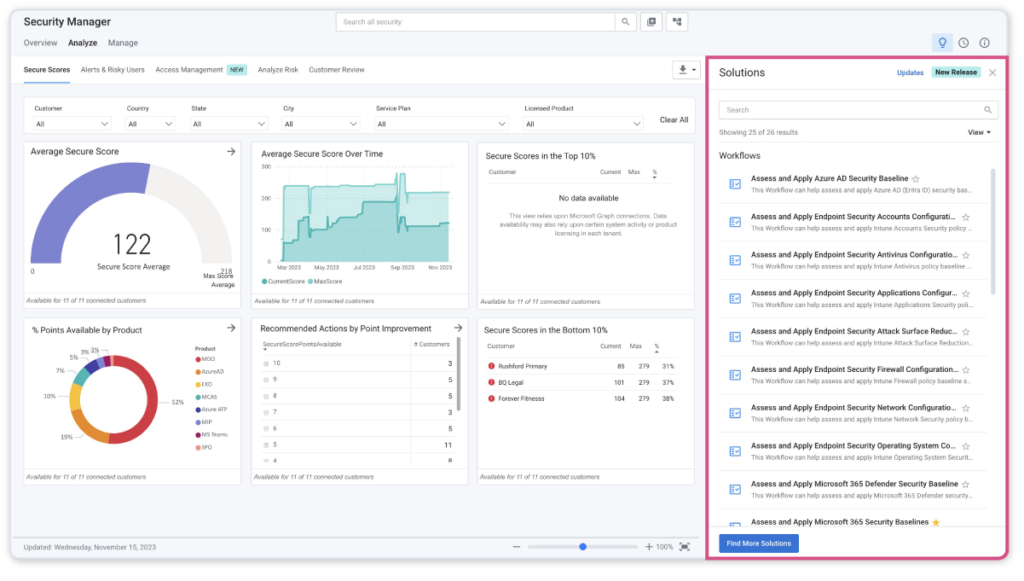
Additionally, you can navigate to the library of all workflows by going to Security Manager => Manage => Workflows:
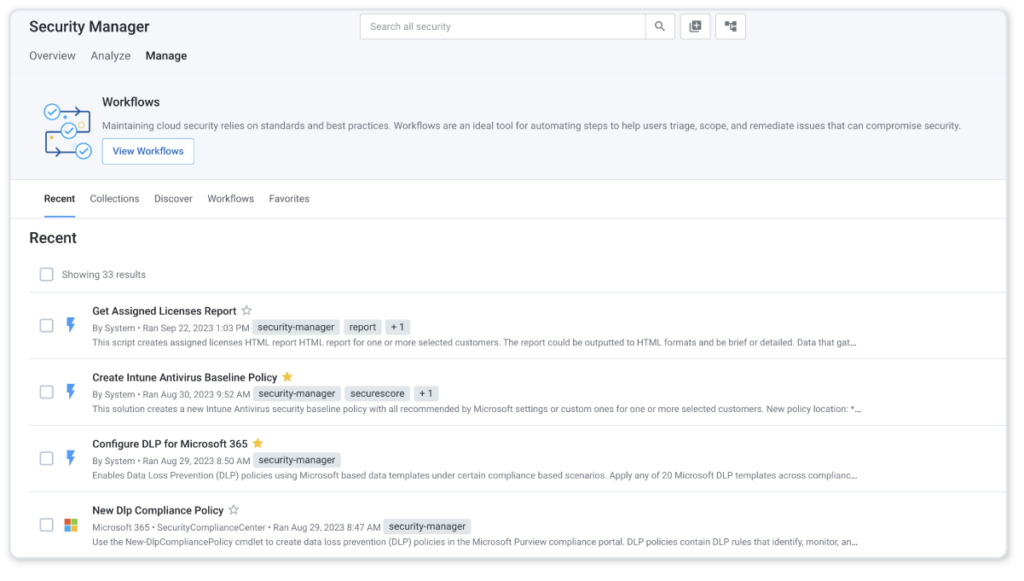
Here, you will be able to interact with workflows before deciding which customers to run them on. This section is great for familiarizing your team with the workflows available. You can also mark workflows “Favorite”, save different versions of them, and even create your own.
Knowing the Solution: Full Documentation within Workflows
In addition to the powerful automation that workflows deliver, each workflow contains a wealth of information about each workflow to enable you, your team, and your customer make informed decisions about a solution.
Each member in your practice who is providing these services to your customers needs the expertise to know where to look to execute a solution, what to look for, and how to perform the action.
Additionally, many workflows have customizable options, so knowing how to choose the right options for each customer is important. And with such a wide range of security solutions that top MSP’s must provide, the right tool be one that enables you and your team to provide a VIP experience to your customers.
Security Manager was designed to empower you to deliver this VIP experience. Each Security Manager workflow contains explanations, or “Notes” at every level. These notes contain full transparency about what each command does, what options are available, and even allow you to drill down into the code it will run.
Workflow notes document the current recommended best practices by Microsoft, and also advise you on how to consult with your customer about the solution, all in one place. Each command within the workflow is documented as well, allowing you to customize each step of a workflow based on customer needs or the situation, should you choose. However, each workflow is set to Microsoft’s recommended best practices by default.
For example, one valuable security milestone for an MSP and their customer is to ensure that Multifactor Authentication (MFA) is enabled. In your Analyze Dashboard, perhaps you have identified a customer who does not have MFA fully configured for all users. After seeing this, your next step can be to Solve it.
But best practices regarding enabling MFA involves several steps. Within the MFA workflow entitled “Research and Configure Multifactor Authentication”, the “Notes” section on the right has a full description of each command, along with instructions, best practices, and tips for making decisions with your customer.
Customers typically understand the importance of this setting given the risks and best practices in today’s world. However, customers likely do not know the options and recommendations available to each of their end users.
This Notes section empowers you to deliver the right recommendations to each of your customers. The MFA workflow’s Notes section contains over 9 Word doc pages of documentation. It’s not necessary to review this information prior to running the workflow, however this is available as an asset to answer any questions your team or customer may have to provide a consistent offering to all your customers.
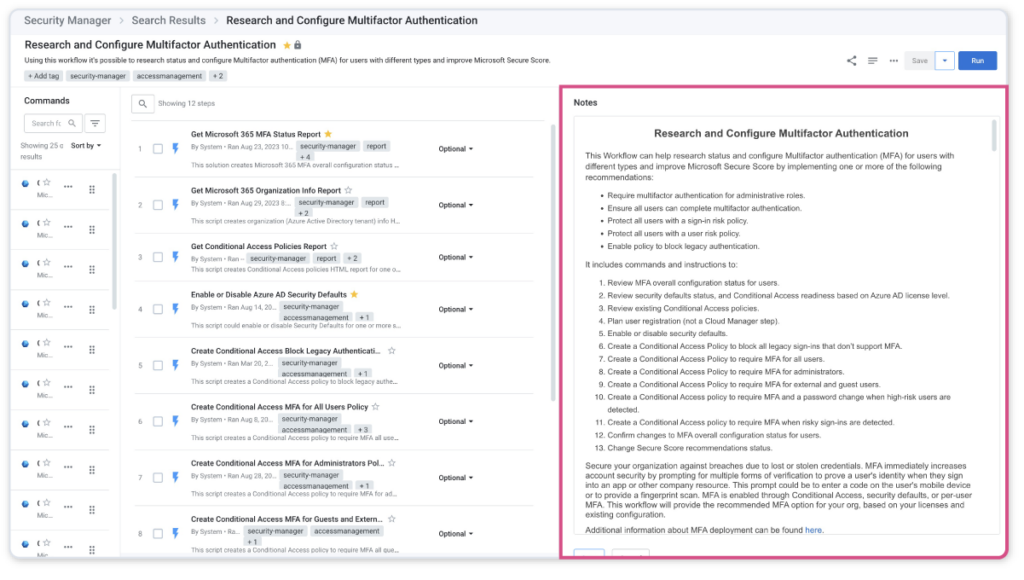
We hope you learned how “Solving it” in security management is made easy with Security Manager. The number of powerful workflows available allows MSPs to provide a comprehensive cyber-security offering, and the notes available at every level empower your team with valuable information that helps deliver consistent intelligent customer protection to customers.
Customers value the information, expertise, and options provided by MSPs using Security Manager. Whether you’re helping them through an incident, handling a simple request, or providing proactive protection, Security Manager empowers you to efficiently “Solve it.”


