How Top Partners Manage Email Phishing Security with 1 Automated Workflow
It’s no secret, the most common successful cyber-crimes target the end user. Phishing emails are designed to trick users by sending an email that appears legitimate or from a trusted sender, with the intent to steal sensitive information or gain access to sensitive systems, or worse.
So how do we really provide continuous protection for and detection of phishing attacks? End-user training and awareness can only go so far. While M365 provides many built-in reports and tools to run against a customer, it requires someone who knows what to run, the expertise to run it, a reminder to do so regularly and to show your work. It can be a real challenge to take these steps…for each customer individually.
Security Manager was built to simplify your security practice, to reduce the cost and toil of performing routine maintenance, and to show your customers the value you’re bringing to their security over time.
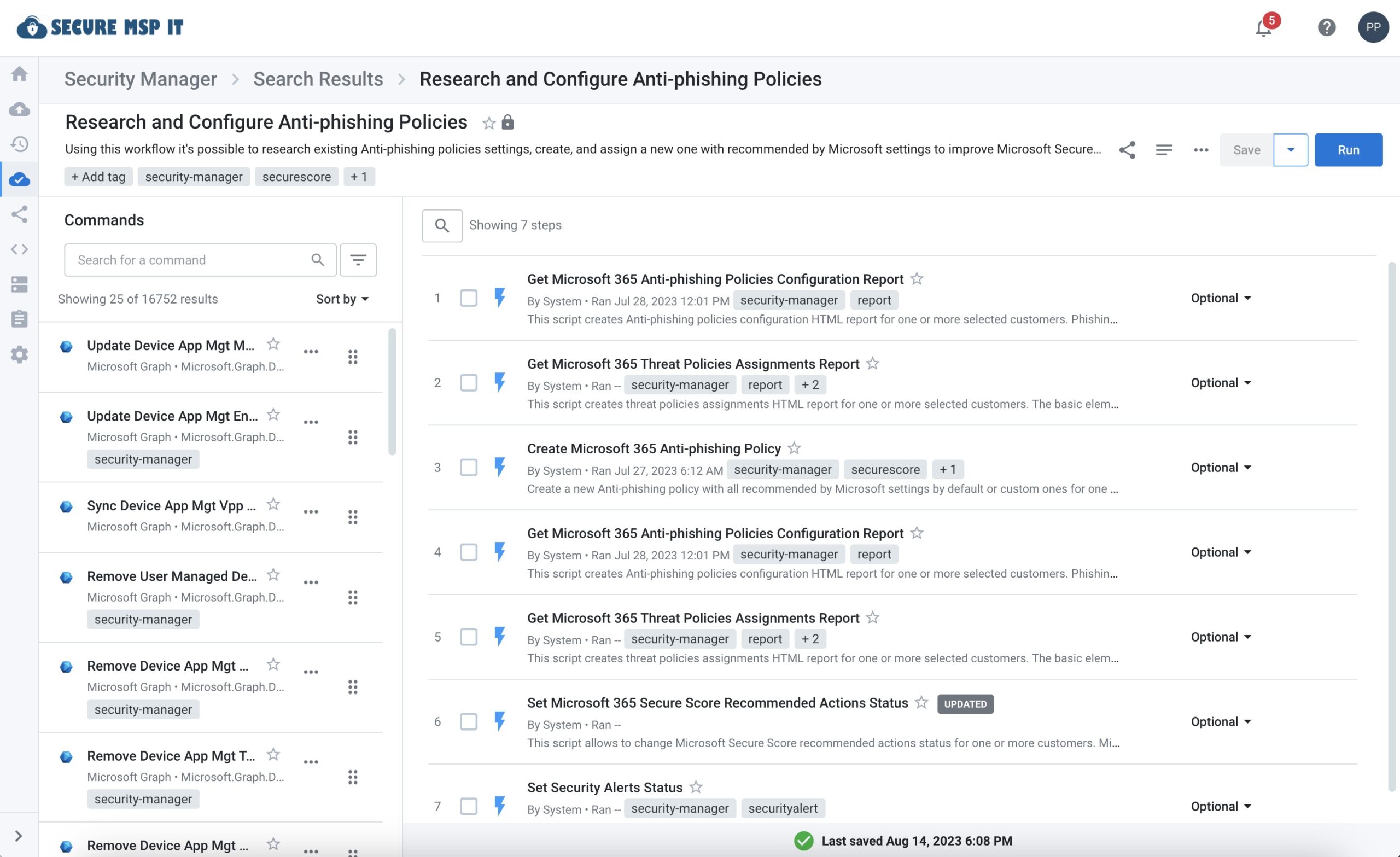
So SkyKick built the workflow: “Research and Configure Anti-Phishing Policies”. This workflow allows you to detect, prevent, report on, and quarantine phishing attacks. It contains 7 powerful steps, each containing dozens of commands, all defaulting with Microsoft recommended best practices. And like all Security Manager workflows, the following options are available to help you realistically scale your security practice:
Workflow Options
- Schedule the workflow, once or recurring
- Specify reporting outputs & format, including 1 or many customers per report
- Fully customizable: Add, remove, or change the workflow to fit your needs
- Option to remediate vulnerabilities or simply report on them
- Specify risk thresholds
- Run against one, many, or all of your customers
A popular best practice by SkyKick Partners is to set this Research and Configure Anti-Phishing Policies report to automatically run against all of their customers every day, aggregating all of their customers and end users into one Excel spreadsheet. By specifying within the report what risk levels to include, they can receive a report for only at-risk users. This automation effectively does an audit of their entire customer base, remediates any phishing risks, and provides reporting against outstanding issues.
Additional reporting is also available to review what changes were made to each tenant, to demonstrate the value they’re bringing to keeping their customers’ M365 tenants secure and incident-free.
Phishing is just one aspect of cyber security, but one that is popularly known by customers as being a key vulnerability. Being able to provide a customer peace of mind that you’re continually monitoring and acting on their M365 tenant’s security is a great way to demonstrate value to your customers and prospective customers.
And it is all included as just 1 of many areas within Security Manager.


