Security is top of mind for customers, partners and the technology vendors in the ecosystem. With so many security attacks originating in compromised passwords, Microsoft has made basic authentication the chief villain to target. Back in October 2022, Microsoft began a campaign to forcibly retire basic authentication in batches for access to M365-tenant services, but provided limited exceptions for partners to continue using legacy authentication. Starting the first week of January 2023, basic auth use will be disabled permanently, with no exceptions available. [See Basic Authentication Deprecation]. In this article, we cover how partners can get ahead of this important challenge, address customer concerns and turn a headwind into a tailwind.
Stepping back, customers often like the convenience of simply typing a password with Basic Auth, so its use can be widespread in many cases and customers are often hesitant to adopt Modern practices like Multi-factor Authentication. Savvy partners have long realized how this “convenience” also increases the risk of stolen credentials and the exposure for both the client and the partner’s broader MSP practice. Partners can leverage these new Microsoft changes as an opportunity to overcome objections and upgrade security for these clients. And there is good reason to be proactive about engaging customers and switching them to Modern Authentication now. Starting January 1, 2023, there may be many end-users who are not able to access their company’s Microsoft 365 tenant, resulting in a significant number of support tickets for partners and unexpected business disruption for customers.
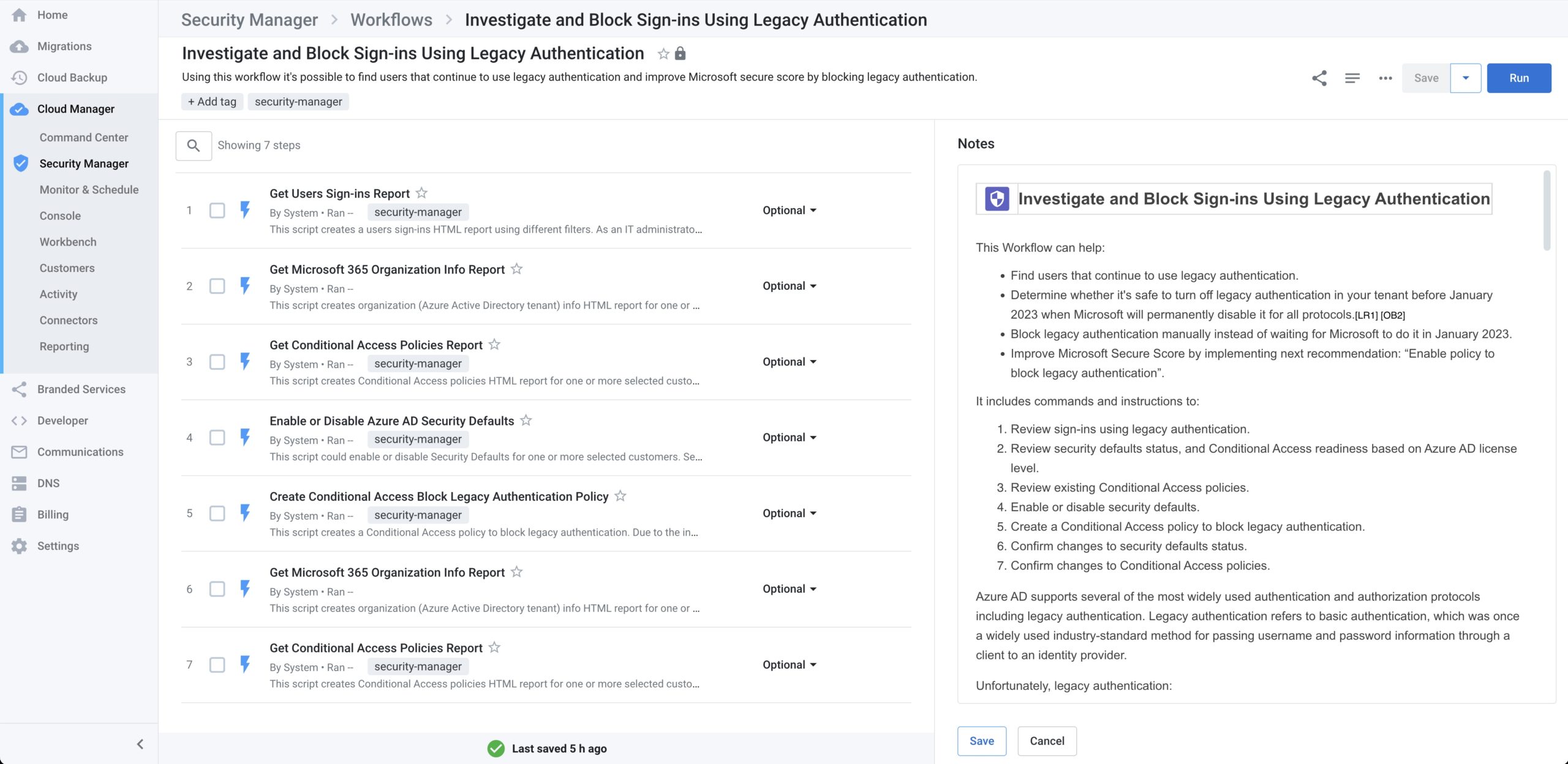
To help partners proactively avoid this potential support desk hit and at the same time help their customers avoid unnecessary business disruption, SkyKick Security Manager has just released an automation workflow that can be used to investigate and block sign-ins using legacy authentication. This workflow was purpose built for MSPs to find, fix and automate this remediation scenario.
The “Investigate and block sign-ins using legacy authentication” is a simple, no-code workflow that provides a set of automations that enable users to perform the following across any number of customers:
- Find users that continue to use legacy authentication.
- Determine whether it’s safe to turn off legacy authentication in your tenant before January 2023 when Microsoft will permanently disable it for all protocols.
- Block legacy authentication proactively instead of waiting for Microsoft to do it in January 2023.
- Improve Microsoft Secure Score by implementing next recommendation: “Enable policy to block legacy authentication”. This gives partners a powerful talking point to engage the customer and recast this “inconvenience” as a “customer benefit” on partners are delivering on security.
Simply refer to the instructions, select the steps you want to perform, and click Run.