Mastering the Top 4 M365 security scenarios for cybersecurity standards: NIST, CIS, Essential 8, Cyber Essential and more compliance
In the conversations we’ve had with hundreds of partners, a consistent theme emerges. Cybersecurity and compliance standards are becoming closer to a requirement in more and more countries. This is no longer an Enterprise thing, 84% of security and IT professionals in SMB list compliance as a mandatory requirement for their business. A commitment to these standards is not just a legal obligation, it is a strategic imperative that underpins an organization’s reputation, sustainability, and long-term success.
MSPs often have to carry this burden on behalf of customers and stay on top of this new evolving landscape. The good news is that while the overall IT spending might be flat or down in SMB, there is appetite and willingness to pay for cybersecurity and compliance solutions. According to a recent study sponsored by McKinsey, 42% of IT decision makers have plans to increase their cybersecurity and compliance spending.
With so many standards to contemplate, NIST, CIS controls, Australia Essential Eight, UK Cyber Essentials, GDPR, GLB, just to name a few, partners and customers alike are asking where do I start? How to simplify the complexity in these standards and add value to my customers?
Two key questions many MSPs are asking:
- What does all this compliance mean to me in my day-to-day conversations with my SMB customers?
- What automation solutions can help meet compliance standards easily for my customers?
SkyKick has done extensive work analyzing hundreds of controls across multiple compliance standards such as CIS controls, Australia Essential 8, UK Cyber Essential. We are attempting to de-mystify the complexity of compliance standards down to these four scenarios:
- Have left to right visibility on where the customers are in M365 baselines
- Tune up MFA and other access and control parameters
- Mailbox hardening
- Core to the standard is a commitment to privacy and Data Loss Prevention (DLP)
If partners can master the Top 4 M365 security scenarios, they will be in good shape to help meet cybersecurity and compliance standards.
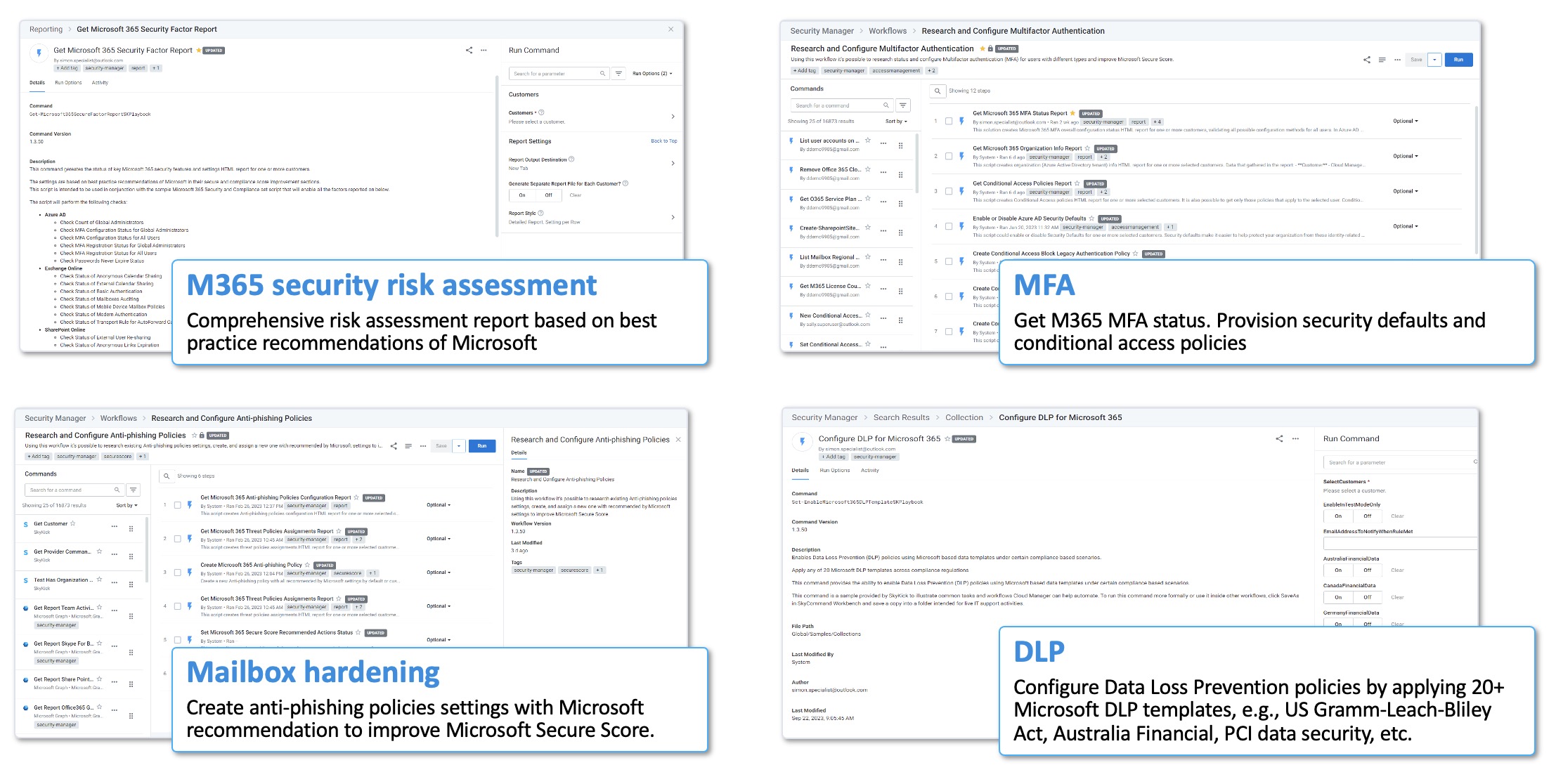
We built a powerful automation application, Security Manager, to make it super easy to deliver on this promise. Let’s see it in action:
Microsoft 365 Security Risk Assessment
Gain total visibility: Effective tooling to be able to see ahead and around the bends to get a full picture on where the vulnerabilities are in the system – within your walls and at the customer. And do this proactively, ahead of getting hit with reactive tickets. “Get Microsoft 365 Security Baselines Report” itemizes more than 150 baseline settings across Azure AD (Entra ID), Exchange Online, SharePoint Online, Teams, Microsoft 365 Defender, and Intune. For those that are not set up according to Microsoft best practices, the report indicates what the settings should be.
In this video segment, we showed five such scenarios: number of global admins, MFA status, SMTP authentication, missing connectors and opportunities to uplevel Microsoft licensing conversations with customers.
Multi-Factor Authentication (MFA)
Access and control is foundational to meeting compliance standards. In fact, both CIS controls and Australia Essential 8 explicitly called out MFA as a compliance category. Analyzing data from millions of user under management in Security Manager, 70% of SMB users do not have MFA configured or configured according to best practice.
Depending on M365 licensing, customers will have different MFA recommended methods such as Security Defaults or Conditional Access. In this video segment, we showed various scenarios in setting up MFA and how Security Manager provides 1-click automation to apply MFA across multiple tenants quickly and easily.
Mailbox Hardening
9 out of 10 cyberattacks start with a phishing email. Mailbox remains an attractive attack vector. Security Manager uses smart approaches and automation to deliver solutions – fast, efficiently and consistently.
In this video segment, we showed how Security Manager can easily create M365 anti-phishing policies across all your customers with out of box 1-click automation. But that’s not all. In the product, you could do the same creating comprehensive policies hardening mailboxes such as anti-spam, anti-malware, safe links and safe attachments.
Data Loss Prevention (DLP)
Data regulation has continued to evolve over the past few years to meet the emerging threats. Regulatory compliance is becoming closer to a requirement in more and more countries. One core component of regulatory compliance is a focus on privacy. You can’t have privacy if the way you are handling data in your tenant is not compliant with appropriate privacy standard. The way you get to privacy from a technology standpoint is to have DLP. DLP is not just a button, DLP is 22 different standards, there are more, but these 22 are what Microsoft made it easy to implement. We boil all of this down in Security Manager so you can apply DLP easily.
Just last week, we hosted a webinar to de-mystifying the complexity of compliance standards. Here is the OnDemand link to the webinar. If you missed it, we welcome you to check it out. It was one of our best attended webinars. You will walk away with the confidence to build a proactive security practice:
- Get a basic understanding of key cybersecurity and compliance standards in various geographies
- Assess the security and data protection needs of your customers.
- Streamline your security practice with cross-tenant tools & scheduled automation.
- Increase customer engagement, retention, and loyalty with data-driven insights.
Take the Self-Guided Tour


